vpcs telnet
I’m a developer, I deploy to a VPC, but what’s going on in there…
我是开发人员,我部署到了VPC,但是那里发生了什么……
受众与目标 (Audience and Aim)
This article is aimed at developers using AWS looking to understand how VPCs work. In many companies the complex infrastructure provisioning is separated from the development process. You may be deploying into a VPC, but not really know where your code is going.
本文针对使用AWS的开发人员,他们希望了解VPC的工作原理。 在许多公司中,复杂的基础架构配置与开发过程是分开的。 您可能正在部署到VPC中,但并不真正知道代码的去向。
Here we will explain at a very high level how a VPC functions. We will assume a small amount of networking knowledge, but the idea is to make the explanation as clear and practical as possible.
在这里,我们将在很高的层次上解释VPC的功能。 我们将假设少量的网络知识,但是其想法是使解释尽可能清晰和实用。
论据 (Argument)

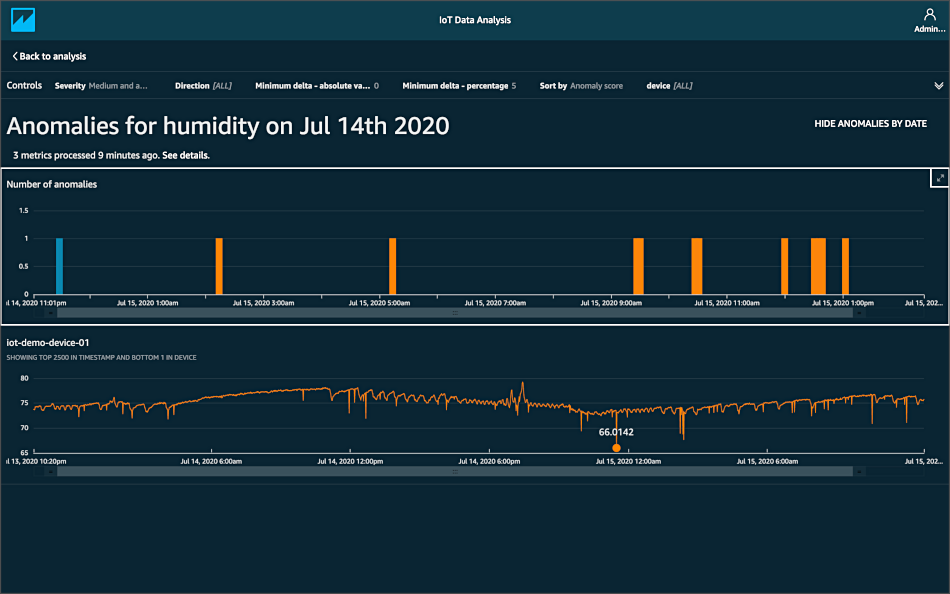
Above is a basic VPC setup which, admittedly, looks a bit daunting at first. Let’s break it down into the component parts and explain how they fit together.
上面是一个基本的VPC设置,首先,看上去有些令人生畏。 让我们将其分解为各个组成部分,并说明它们如何组合在一起。
区域和可用区 (Regions and Availability Zones)
A Region is a physical location somewhere round the world where data centres are clustered. For example, Ireland is the eu-west-1 region. Within a region there are groups of logical data centres called Availability Zones. Each AWS region consists of multiple, isolated, and physically separate availability zones within a geographic area. For example, eu-west-1 has three separate availability zones: eu-west-1a, eu-west-1b and eu-west-1c!
区域是数据中心聚集在世界各地的物理位置。 例如,爱尔兰是eu-west-1地区。 在一个区域内,有称为可用区的逻辑数据中心组。 每个AWS区域均由一个地理区域内的多个,隔离且物理上分开的可用性区域组成。 例如, eu-west-1具有三个单独的可用区: eu-west-1a, eu-west-1b和eu-west-1c !
Each VPC is based in a given region, but spans over all availability zones within that region. This allows you to architect for resilience in the case that one of the availability zones goes down.
每个VPC都位于给定区域中,但跨越该区域内的所有可用性区域。 这样,当其中一个可用区出现故障时,您就可以设计弹性以应对各种情况。
In our example architecture we have a VPC within a region and then two availability zones within that VPC.
在我们的示例架构中,我们在一个区域内有一个VPC,然后在该VPC中有两个可用性区域。
VPC (VPC)
This is essentially a group of IP addresses we reserve within a region. Initially, we need to select a CIDR block (a system I don’t think I’ll ever understand), which will give us the range of IP addresses we can use. It is common to use /16 for the VPC and then use smaller ones for the subnets.
这实际上是我们在一个区域内保留的一组IP地址。 最初,我们需要选择一个CIDR块 (一个我认为我不会理解的系统),这将为我们提供可以使用的IP地址范围。 对于VPC,通常使用/16 ,然后将较小的子网用于子网。
For example, we may use 10.0.0.0/16. This will give us the IP addresses 10.0.0.0-10.0.255.255 (around 65,536 of them).
例如,我们可以使用10.0.0.0/16 。 这将为我们提供IP地址10.0.0.0-10.0.255.255 (其中约65,536个)。
公共子网 (Public Subnet)
Subnets are a group of IP addresses we reserve within our VPC IP addresses. We normally follow the convention 10.0.x.0/24, where x is increasing for each new subnet. In this example we will use public subnets with the CIDR blocks 10.0.1.0/24 and 10.0.2.0/24, which gives us the ranges 10.0.1.0–10.0.1.255 and 10.0.2.0–10.0.2.255.
子网是我们在VPC IP地址中保留的一组IP地址。 我们通常遵循惯例10.0.x.0/24 ,其中x对于每个新子网都在增加。 在这个例子中,我们将使用公共子网与CIDR块10.0.1.0/24和10.0.2.0/24 ,这让我们的范围10.0.1.0–10.0.1.255和10.0.2.0–10.0.2.255 。
We would then associate the subnets with a route table that sends all traffic to the internet gateway (covered below). It is this that allows us to route traffic out to the wider internet, and this that makes it a public subnet.
然后,我们将子网与路由表相关联,该路由表将所有流量发送到Internet网关(在下面介绍)。 正是这一点使我们能够将流量路由到更广泛的Internet,并使之成为公共子网。
专用子网 (Private Subnet)
Similarly we can make private subnets. In this example we have two types of private subnets; one for the application layer and one for the database layer. We can assign them the CIDR blocks 10.0.3.0/24 , 10.0.4.0/24 10.0.5.0/24 and10.0.6.0/24. All of these will then route out to the NAT gateway using route tables (described later).
同样,我们可以建立专用子网。 在此示例中,我们有两种类型的专用子网: 一种用于应用程序层,另一种用于数据库层。 我们可以为他们分配CIDR块10.0.3.0/24 , 10.0.4.0/24 10.0.5.0/24和10.0.6.0/24 。 然后,所有这些都将使用路由表(稍后描述)路由到NAT网关。
NAT网关 (NAT Gateway)
Network Address Translation (NAT) Gateways are used to enable instances in a private subnet to connect to the internet or other AWS services, but prevent the internet from initiating a connection with those instances.
网络地址转换(NAT)网关用于使私有子网中的实例能够连接到Internet或其他AWS服务,但阻止Internet启动与这些实例的连接。
In our example we want to create a new NAT Gateway inside our public subnet. To do this we will need an elastic IP address for the gateway in order to have a static IP address to route to, something we provision separately.
在我们的示例中,我们要在公共子网中创建一个新的NAT网关。 为此,我们将需要网关的弹性IP地址,以便将静态IP地址路由到我们单独提供的某个地址。
亚马逊EC2 (Amazon EC2)
Amazon EC2 is ‘a web service that provides secure, resizable compute capacity in the cloud’. For the purpose of our example we will think of it as a server in the cloud we can deploy code into. They come in many shapes and sizes though, so it is worth researching them independently to see what the offerings are.
Amazon EC2是“在云中提供安全,可调整大小的计算能力的Web服务”。 就我们的示例而言,我们将其视为可以在其中部署代码的云中的服务器。 它们具有多种形状和尺寸,因此值得独立研究它们以了解产品。
亚马逊极光 (Amazon Aurora)
Amazon Aurora is a cloud-based relational database running both MySQL and PostgreSQL. It is a fully managed Amazon Relational Database Service (RDS), which essentially means we provision an Aurora cluster and AWS helps keep it alive.
Amazon Aurora是同时运行MySQL和PostgreSQL基于云的关系数据库。 它是一个完全托管的Amazon Relational Database Service(RDS) ,从本质上讲 ,这意味着我们预配了Aurora集群,而AWS则帮助其保持活动状态。
In our example we have a master/ replica set up, where the master database is in the first availability zone, but the replica is in the second. This gives us a level of resilience as if the first availability zone goes down as we can failover to the second.
在我们的示例中,我们设置了一个主数据库/副本数据库,其中主数据库位于第一个可用性区域中,而副本数据库位于第二个可用区域中。 这给了我们一定程度的弹性,好像第一个可用性区域出现故障时一样,因为我们可以故障转移到第二个可用性区域。
53路 (Route 53)
Route 53 is a way of registering a DNS entry for our VPC. We buy a domain name and then point this to our load balancer.
路由53是为我们的VPC注册DNS条目的一种方式。 我们购买一个域名,然后将其指向我们的负载均衡器。
For example, we may buy vpcexample.com. It is then relatively easy to direct any traffic from that DNS to our load balancer, a process we will cover below.
例如,我们可以购买vpcexample.com 。 然后,将来自该DNS的任何流量定向到我们的负载均衡器相对容易,我们将在下面介绍这一过程。
互联网网关 (Internet Gateway)
An internet gateway is the component responsible for allowing communication between your VPC and the internet.
Internet网关是负责允许您的VPC与Internet之间进行通信的组件。
An internet gateway serves two purposes:
互联网网关有两个作用:
- To provide a target in your VPC route tables (covered below) for internet-routable traffic. 在VPC路由表(如下所示)中提供可路由Internet的目标。
- To perform network address translation (NAT) for instances that have been assigned public IPv4 addresses. 对已分配了公共IPv4地址的实例执行网络地址转换(NAT)。
路线表 (Route Tables)
We use Route tables in our example to direct traffic from a subnet. There are three subnets of two different types in our VPC design.
在示例中,我们使用了路由表来引导来自 一个子网。 在我们的VPC设计中,存在三个具有两种不同类型的子网。
Route table for the public subnet: This is used to route traffic from the public subnet out through the internet gateway. In the below this routes all traffic for IP addresses in the VPC to ‘local’, whereas anything else goes out through the internet gateway.
公共子网的路由表:用于将流量从公共子网通过Internet网关路由出去。 在下面,这会将VPC中IP地址的所有流量都路由到“本地”,而其他任何内容都通过Internet网关流出。
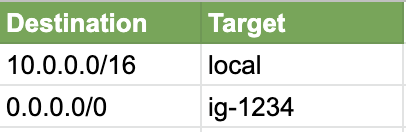
Route table for private subnets: This is used to route traffic from the private subnets to the NAT gateway. In the below this routes all traffic for IP addresses in the VPC to ‘local’, whereas anything else goes to the NAT gateway, which in turn goes out through the internet gateway.
专用子网的路由表:用于将流量从专用子网路由到NAT网关。 在下面,这会将VPC中IP地址的所有流量都路由到“本地”,而其他所有流量都到达NAT网关,后者又通过Internet网关出去。

Subnets are explicitly associated with a route table.
子网与路由表明确关联。
安全组 (Security Groups)
A security group controls inbound and outbound traffic for an instance. When you launch an instance in a VPC you can assign up to five security groups. Security groups do not act at the subnet level. Therefore, each instance in a subnet can be assigned to a different set of security groups.
安全组控制实例的入站和出站流量。 在VPC中启动实例时,您最多可以分配五个安全组。 安全组不在子网级别起作用。 因此,可以将子网中的每个实例分配给一组不同的安全组。
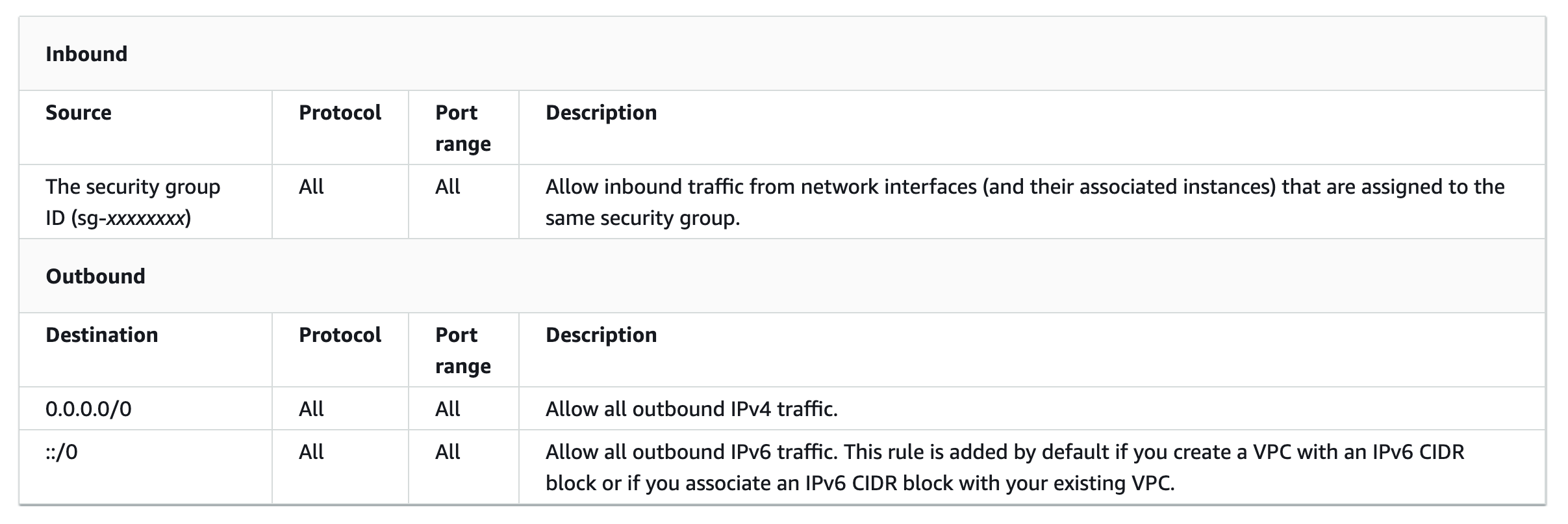
For our example architecture we will need two security groups.
对于我们的示例架构,我们将需要两个安全组。
Security Group A: For the load balancer to accept all incoming traffic. This will accept all traffic (
0.0.0.0/0) to web ports80/443.安全组A:负载平衡器接受所有传入流量。 这将接受到Web端口
80/443所有流量(0.0.0.0/0)。Security Group B: For the EC2 instances to accept connections from the load balancer. This will accept all traffic from the load balancer security group to web ports
80/443.安全组B: EC2实例接受来自负载平衡器的连接。 这将接受从负载平衡器安全组到Web端口
80/443所有流量。
We then associate Security Group A with the load balancer and associate Security Group B with all of the EC2 instances.
然后,我们将安全组A与负载均衡器相关联,并将安全组B与所有EC2实例相关联。
网络访问控制列表(NACL) (Network Access Control List (NACL))
Network Access Control Lists are attached to subnets and specify a range of IP address based rules. To use an example:
网络访问控制列表附加到子网,并指定基于IP地址的规则范围。 举个例子:
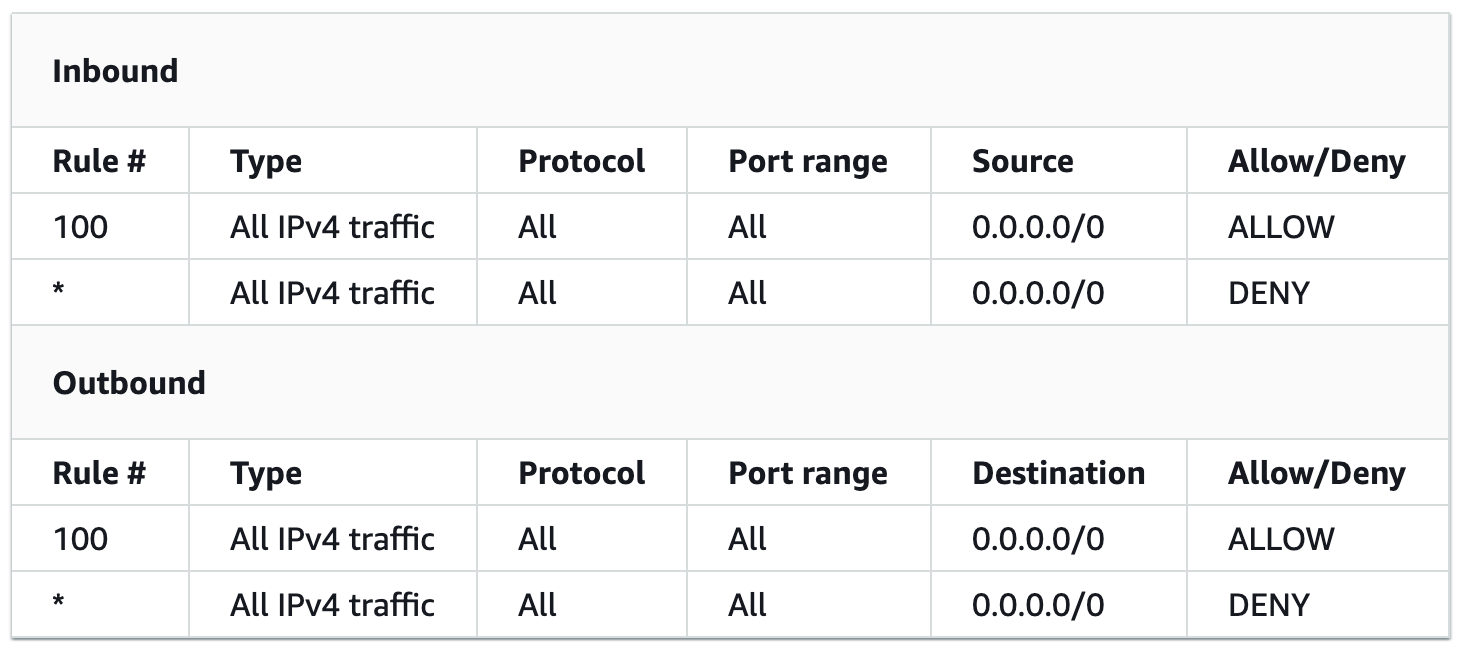
The above demonstrates a NACL which allows all outgoing and ingoing IPv4 traffic for a subnet. Rules are processed in rule number order. In both cases rule 100 takes precedence over the starred rule.
上面展示了一个NACL,它允许子网的所有传出和传入IPv4流量。 规则以规则编号顺序处理。 在这两种情况下,规则100都优先于已加星标的规则。
We could have NACLs for the private and public subnets with similar constraints to the security groups, only using IP addresses. However, this is duplication of effort and so a common pattern is just to allow anything in the NACLs and then limit accessibility in the security groups.
仅使用IP地址,我们就可以为私有和公共子网设置与安全组具有类似约束的NACL。 但是,这是重复的工作,因此一个通用的模式只是允许NACL中的任何内容,然后限制安全组中的可访问性。
应用程序负载均衡器 (Application Load Balancer)
The application load balancer is used to distribute traffic amongst instances in our application subnet. For our example we have two EC2 instances spread over two availability zones and would like to share any incoming requests between them both.
应用程序负载平衡器用于在我们的应用程序子网中的实例之间分配流量。 对于我们的示例,我们有两个分布在两个可用性区域中的EC2实例,并且希望在它们之间共享任何传入的请求。
Load balancers can be both internet facing or internal. Internet facing load balancers are used to balance traffic coming in from the open internet (in our example via Route 53), whereas internal load balancers are for components contained within our VPC.
负载平衡器可以是面向Internet的,也可以是内部的。 面向Internet的负载平衡器用于平衡来自开放Internet的流量(在我们的示例中通过Route 53),而内部负载平衡器用于VPC中包含的组件。
The configuration of a load balancer includes:
负载均衡器的配置包括:
A listener configuration: This describes which ports to listen on and whether or not we should be using
httporhttps.侦听器配置:这描述了要侦听的端口以及我们是否应该使用
http或https。The availability zones and subnets: If it is an external load balancer it should be in the public subnet — an internal load balancer can be in the private one. A common pattern (and the one we use in our example) is to have the load balancer spread across multiple availability zones and for it to be a single point of contact for external connections.
可用性区域和子网:如果它是外部负载均衡器,则应位于公共子网中-内部负载均衡器可以位于私有子网中。 一种常见的模式(以及我们在示例中使用的模式)是使负载均衡器分布在多个可用区域中,并使该负载均衡器成为外部连接的单点接触点。
A security group: This ensures it only allows connections to and from specified locations. In the above we want to accept all incoming traffic, but only want to route outgoing traffic to our EC2 instances.
甲 安全组 :这确保它只允许向和从指定的位置的连接。 在上面,我们要接受所有传入流量,但只想将传出流量路由到我们的EC2实例。
自动伸缩组 (Autoscaling Groups)
Autoscaling groups define a minimum, maximum and preferred amount of a certain type of EC2 instance we would like available. It works in conjunction with scaling policies to alter the number of these instances in accordance with certain criteria.
自动伸缩组定义了我们希望可用的某种类型的EC2实例的最小,最大和首选数量。 它与扩展策略结合使用,以根据某些条件更改这些实例的数量。
The components of an autoscaling group are as below:
自动伸缩组的组件如下:
Load Balancer: This is the load balancer we would like to aim towards the autoscaling group.
负载均衡器:这是我们要针对自动伸缩组的负载均衡器。
Health Check: This is responsible for making sure each of the instances are up and alive, removing the instances from the group if they are not. Often this comes in the form of an
httpcall to an endpoint on the box. If the box is unresponsive it will return nothing from this endpoint!运行状况检查:负责确保每个实例都正常运行,如果没有,则将其从组中删除。 通常,这是对包装盒上的端点进行
http调用的形式。 如果该框没有响应,它将不会从该端点返回任何内容!Launch Template: The idea of an autoscaling group is that we would like to keep a number of identical instances available. In order to be able to launch a new EC2 we need a description of what it should look like. This is the purpose of a launch template.
启动模板:自动扩展组的想法是,我们希望保持许多相同的实例可用。 为了能够启动新的EC2,我们需要对其外观进行描述。 这是启动模板的目的。
Scaling Policies: Autoscaling groups are often used in order to be able to scale up our infrastructure in the case of increased traffic. Scaling policies define these rules. For example we may want to add a new instance if the CPU Utilisation across an autoscaling group is above 80%. We can then scale down if the CPU Utilisation goes below 80% again.
扩展策略:为了在流量增加的情况下扩展我们的基础架构,经常使用自动扩展组。 扩展策略定义了这些规则。 例如,如果跨自动扩展组的CPU利用率超过80%,我们可能想添加一个新实例。 然后,如果CPU利用率再次低于80%,我们可以缩小规模。
Network: We know what we’re launching from the launch template. We know when we’re launching from the scaling policies. We just need to know where we’re launching! This is the duty of the network configuration, which specifies the subnets to launch to.
网:我们知道我们正在从发射模板启动。 我们知道何时从扩展策略启动。 我们只需要知道要在哪里发射! 这是网络配置的职责,它指定要启动的子网。
结论 (Conclusion)
To summarise we will follow two imaginary requests through our system, one ingoing and one outgoing.
总而言之,我们将通过系统遵循两个假想的请求,一个传入请求,一个传出请求。
内向请求 (Ingoing Request)
- A client makes a request in order to retrieve some information via an API in our application. 客户发出请求,以便通过我们应用程序中的API检索某些信息。
- This is routed through the DNS entry we created in Route 53 to our application load balancer sitting in our public subnets. The load balancer accepts this traffic as its security group accepts all incoming traffic. 这是通过我们在Route 53中创建的DNS条目路由到位于公共子网中的应用程序负载平衡器的。 负载平衡器接受此流量,因为其安全组接受所有传入的流量。
- Our application load balancer forwards this on to one of our EC2 instances and the application sitting in our private subnets. The EC2 instances accept this traffic as their security group accepts all requests from the load balancer. 我们的应用程序负载平衡器将其转发到我们的EC2实例之一和位于我们专用子网中的应用程序。 EC2实例接受此流量,因为其安全组接受来自负载平衡器的所有请求。
- The application makes a request to the Aurora instance in order to retrieve the information from the database. 该应用程序向Aurora实例发出请求,以便从数据库中检索信息。
- The response is returned back through the system. 响应通过系统返回。
寄出要求 (Outgoing Request)
- Our application on our EC2 instance makes an outgoing request to an external API. 我们在EC2实例上的应用程序向外部API发出传出请求。
- This is routed to the NAT Gateway via the route table. The NAT Gateway then routes the request to the open internet via the Internet Gateway. 它通过路由表路由到NAT网关。 然后,NAT网关通过Internet网关将请求路由到开放的Internet。
- The response is returned. 返回响应。
翻译自: https://medium.com/@jc1175/a-developer-introduction-to-vpcs-9922b9cb08b3
vpcs telnet